Internet Marketing Checklist – 18 Securing Your Account Checklists
in Internet Marketing Checklists , Personal Use Only ProductsChoose Your Desired Option(s)
has been added to your cart!
have been added to your cart!
#securepasswords #securingyouraccount #firewalls #malware #antimalwaresoftware #reputablehosting #serviceattacks
Internet Marketing Checklist – 18 Securing Your Account Checklists
Internet Marketing Checklists by BuyQualityPLR.com
Checklists Created To Help You With Securing Your Account
Use these marketing checklists to simply the process of doing Securing Your Account.
We personally use these checklists when doing our marketing and you can too!
These checklists are delivered in PDF format. So you can print them and use them as a step by step guide of tasks you need to plan and complete while doing Securing Your Account.
It’s much easier to succeed at your marketing if you’re planning properly and these checklists are designed to help you do exactly that.
has been added to your cart!
have been added to your cart!
Introducing…
Internet Marketing Checklist – 18 Securing Your Account Checklists

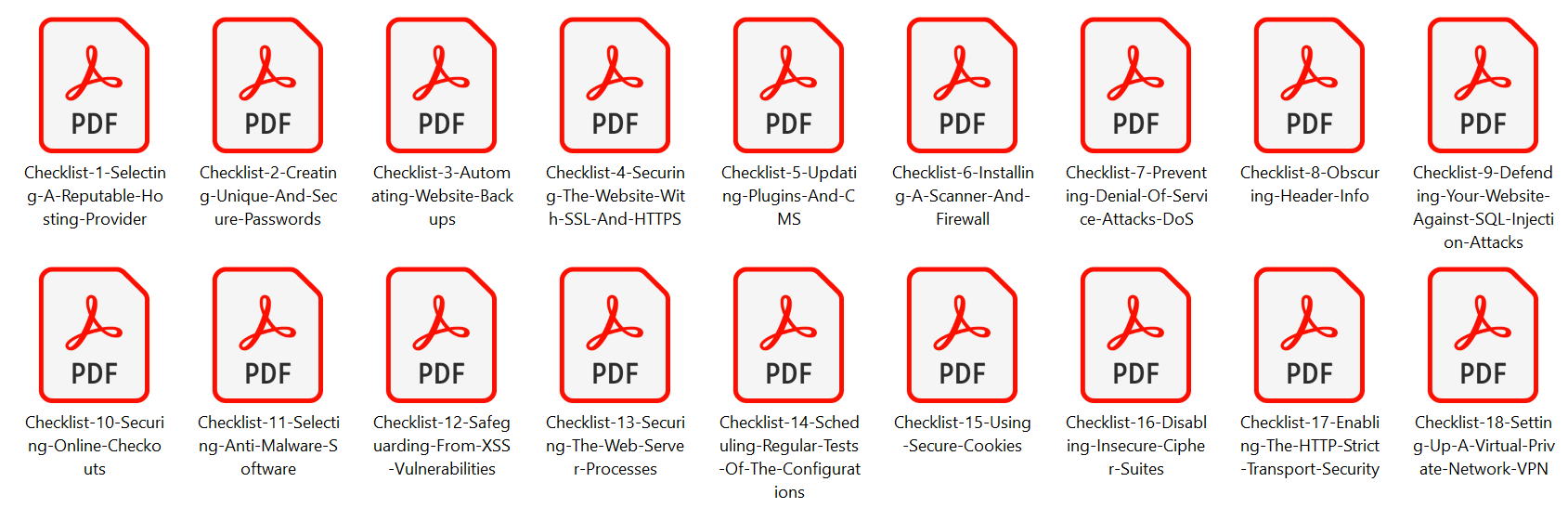
Here’s the List of 18 Securing Your Account Checklists You’ll Get:
Checklist 1 – Selecting A Reputable Hosting Provider
Checklist 2 – Creating Unique And Secure Passwords
Checklist 3 – Automating Website Backups
Checklist 4 – Securing The Website With SSL And HTTPS
Checklist 5 – Updating Plugins And CMS
Checklist 6 – Installing A Scanner And Firewall
Checklist 7 – Preventing Denial Of Service Attacks DoS
Checklist 8 – Obscuring Header Info
Checklist 9 – Defending Your Website Against SQL Injection Attacks
Checklist 10 – Securing Online Checkouts
Checklist 11 – Selecting Anti Malware Software
Checklist 12 – Safeguarding From XSS Vulnerabilities
Checklist 13 – Securing The Web Server Processes
Checklist 14 – Scheduling Regular Tests Of The Configurations
Checklist 15 – Using Secure Cookies
Checklist 16 – Disabling Insecure Cipher Suites
Checklist 17 – Enabling The HTTP Strict Transport Security
Checklist 18 – Setting Up A Virtual Private Network VPN
Here’s the details of the checklists you’ll get in this Securing Your Account checklists pack:
Checklist #1 – Selecting A Reputable Hosting Provider
One of the most important steps to having your websites safe and secure is having a reputable hosting provider that would ensure your safety and personally work with you in case something happens. In this checklist, we go over a list of the most reputable hosting providers you can choose from.
Checklist #2 – Creating Unique And Secure Passwords
It’s obvious you should have a unique and secure password, however, not everyone has one. In this checklist, we go over some tips and tricks that will help you create a strong password.
Checklist #3 – Automating Website Backups
Having an automated website backup is crucial. It ensures you won’t lose your content permanently. In this checklist, we guide you through the steps for setting up automated website backups.
Checklist #4 – Securing The Website With SSL And HTTPS
The SSL is a digital certificate that established a secure link between a server and a web browser. The SSL ensures that any data you pass between a server and a browser is secure and thereby prevents your data from being intercepted by hackers and is crucial for your website’s well-being. In this checklist, we show you how to setup SSLs and HTTPS for your websites.
Checklist #5 – Updating Plugins And CMS
When using themes, scripts, and plugins from a third party, it is always advisable to use updated versions to prevent your data and content management systems from being intercepted by hackers. Further developers often release new updates regularly with new features and new functionalities and further ensure that the updated versions are clear of any vulnerability. As such, it is often advisable to regularly update your software to the latest version. This checklist provides a guide for updating plugins and CMS on your site.
Checklist #6 – Installing A Scanner And Firewall
Installing a firewall and scanner is a vital step in ensuring the safety of your site and your content. A firewall makes it possible for you to scan for potential malicious codes and malware on your site. There are myriad free and paid tools available which is why in this checklist we go over some of the best options.
The denial of service attack DoS refers to attacks that are meant to flood an IP address with exceptionally large volumes of data to render the site’s information systems, emails, online accounts, and other network resources inaccessible by users. DoS attacks are mostly targeted at e-commerce websites such as payment processing companies thereby affecting your site by extension. It is always advisable to take the necessary steps and precautions to mitigate a DoS attack before it happens and in this checklist, we’ll show you exactly how to do that.
Checklist #8 – Obscuring Header Info
When running your web server, the header info, often referred to as the web banner displays the web server version number and its operating system. The web server banner is oftentimes targeted by attackers to send a simple HTTP request to any web application. Further attackers grab the banner and use it to launch attacks on your web server version. To protect your website from being a target of such launched attacks, it is important to consider obscuring your header info and in this checklist, we’ll show you exactly how to do it.
Checklist #9 – Defending Your Website Against SQL Injection Attacks
SQL injections allow hackers to take over your database servers by using whitelist input validation and limiting user permissions among other proactive steps. Through such attacks, hackers can modify the content of a website, as well as steal data that is private and sensitively such as users’ home addresses, personal info, and credit card numbers. This will give you tips and tricks on how to protect yourself from such attacks.
Checklist #10 – Securing Online Checkouts
One of the more sensitive elements of your website is the checkout page. While it is important to ensure that your website is user-friendly, it is equally important to ascertain the security of the website’s online checkouts. Characteristically, websites are susceptible to myriad cyber-crimes and attacks by hackers and as such, it is essential to ensure utmost security for your online checkouts on the website. This checklist addresses the necessary steps and measures to implement in order to secure your checkout.
Checklist #11 – Selecting Anti-Malware Software
There are myriad factors to put into consideration when selecting anti-malware software. It is important to identify the most essential factors of the anti-malware software that are able to effectively protect your website from attackers and repair the website pending an attack. There are various options… Some are free, some are paid… Which is why in this checklist we’ll go over some of the best options.
Checklist #12 – Safeguarding From XSS Vulnerabilities
As a website owner, it is essential for you to reduce your cross-site scripting (XSS) vulnerabilities. XSS refers to a security bug in a website that can make it easy for hackers to introduce malicious JavaScript to the HTML pages that are displayed to users. The XSS is among the most commonly used attacks by hackers to steal sensitive data by altering the functioning of a website and changing the appearance of a website among others. In this checklist, we’ll show you some of the best practices to protect your websites from such attacks.
Checklist #13 – Securing The Web Server Processes
Securing your web server processes minimizes your website’s vulnerability to data hacks and breaches. Web servers are the most targeted hosts in any network owing to the fact that they are publicly accessed and are thus exposed to all kinds of malicious attacks. Securing your web server processes entails ascertaining the security of your basic environment for hosting to protect your software and operating systems from being broken into by hackers. In this checklist, we’ll show you essential tips for maintaining the security of your web server processes.
Checklist #14 – Scheduling Regular Tests Of The Configurations
Configuration testing allows you to identify diagnostic information that helps you identify and eliminate bottlenecks in your website. Configuration tests entail running performance testing on the system to determine its efficiency. These types of tests are not necessarily aimed at identifying bugs and threats; rather, they aim at verifying the system under development under different supported software and hardware to ascertain the best working combinations. In this checklist, we’ll show you exactly how to run such tests.
Checklist #15 – Using Secure Cookies
Cookies play a pivotal role in the functionality of a website in that they can be used for session management, tracking, and tracking a user’s journey. Cookies may contain private and sensitive information (depending on the type) that may be used by hackers for malicious intentions. As such, it is imperative to use secure cookies to prevent interjections from attackers eavesdropping on the channel. In this checklist, we’ll show you how to use secure cookies.
Checklist #16 – Disabling Insecure Cipher Suites
Cipher suites are used to encrypt communications, it is ideal that only the strong and secure ciphers are used. Therefore it is essential for you to disable redundant and weak cipher suites. In this checklist, we’ll provide you a how-to guide for disabling weak and insecure protocols and cipher suites.
Checklist #17 – Enabling The HTTP Strict Transport Security
The HTTP strict transport security (HSTS) primarily instructs user and web browsers to only use secure connections when communicating with a web site. The HSTS is a security setting on your server that prevents malicious activities from hackers including cookie hijacking, SSL protocol attacks, as well as SSL stripping among others. In this checklist, you will find a guide for enabling HSTS on your site.
Checklist #18 – Setting Up A Virtual Private Network (VPN)
A virtual private network offers additional security and privacy that not only allows safe internet access but further protects data and encrypts connections on public networks. The VPN is further instrumental when it comes to providing online anonymity, ensuring your privacy against being tracked when torrenting. Ultimately, VPNs foster convenience for your website and easy administration while at the same time securing your privacy. In this checklist, we’ll go over some of the best VPNs out there.
has been added to your cart!
have been added to your cart!
Start using the checklists right now to save time and improve your marketing or give it to your assistant so they can plan and execute your marketing with proper guides.
You be able to stay focused without having to guess what you need to do next. Get better results with these marketing checklists.
Here’s a Preview of the Securing Your Account checklists pack:
Package Details:
- Checklist
- License
Total File Download Size:
3.55 Megabytes (MB)
Personal Use License:
[YES] Can be used for Personal Use
[YES] Can learn from this product
[YES] Can Use This Product for Marketing Planning
[NO] Can sell this Product
[NO] Can convey and sell Giveaway Rights
[NO] Can convey and sell Resale Rights
[NO] Can convey and sell Master Resale Rights
[NO] Can convey and sell Private Label Rights to the original document
Share Now!